RoltekConnect Cloud Secure Remote Access — Industrial Connectivity Without Compromise
Access your machines, PLCs, and industrial devices securely and instantly from anywhere in the world with RoltekConnect Cloud.
- The Big Picture
Why Remote Access is Critical in Industrial Environments
Downtime is costly. Delayed maintenance, slow troubleshooting, and restricted access can impact product delivery and safety. RoltekConnect removes barriers, enabling real-time, secure remote access to PLCs, HMIs, SCADA systems, and other critical equipment — from wherever you are.
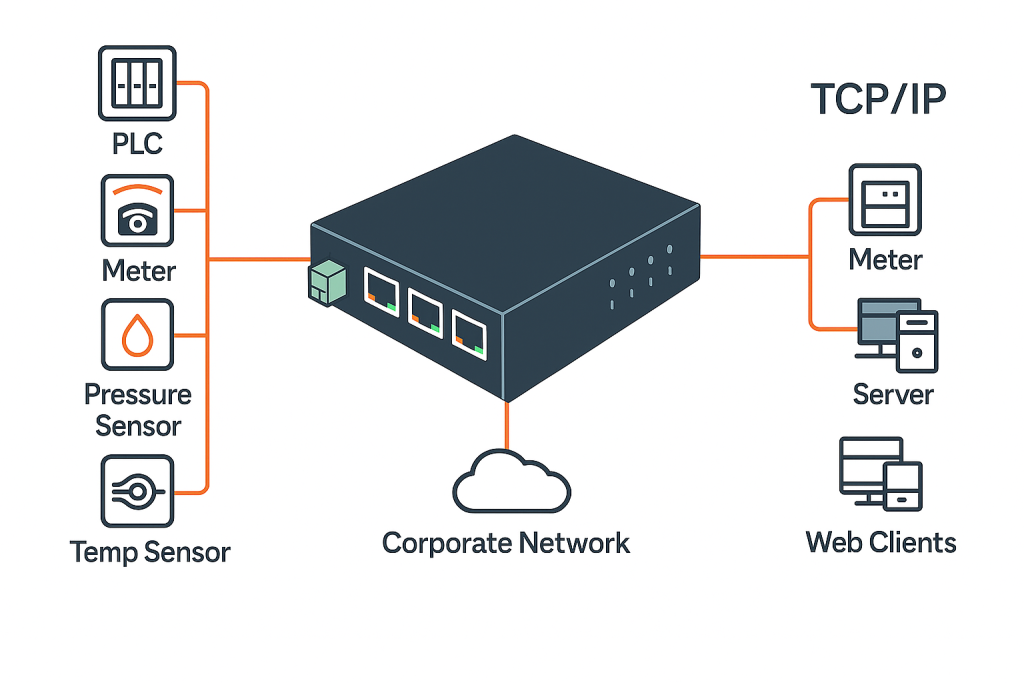
Core Solution & Architecture
Hardware Gateways (RLTK430, RLTK421, RLTK451)
Rugged industrial devices designed to connect with your field equipment securely.

Access Client & Portal:
Web-based or cross-platform clients for technicians; centralized portal for admin users to manage access, sessions, logs.

Network / Connectivity:
Encrypted VPN tunnels, zero trust principles, role-based access, and support for legacy protocols (including serial and USB).
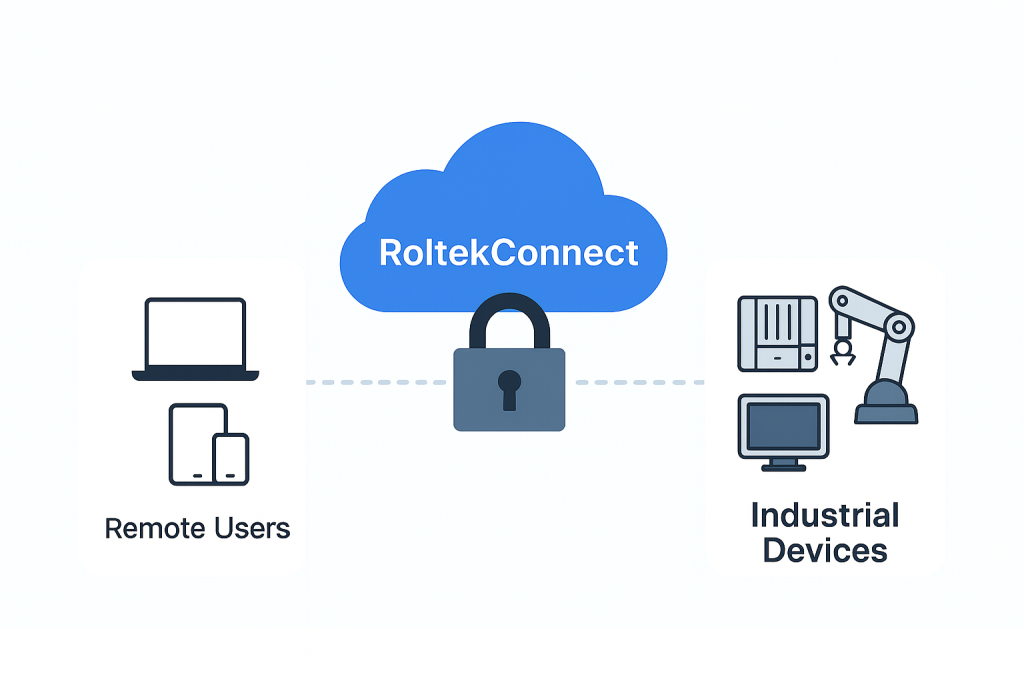
- SECURE REMOTE ACCESS
Industrial Remote Access with a Zero-Trust Tunnel
- Set up in minutes — fast client/agent onboarding.
- Role- and time-based authorization — JIT approvals, temporary access windows.
- Auditable sessions — full logs, live monitoring, instant revoke.
Real-World Scenarios
Remote Maintenance & Troubleshooting
Technicians can program, debug, and adjust machines without visiting the site — reducing travel costs and accelerating problem resolution.
OEM Support & Customer Service
Machine manufacturers can securely access customer systems for proactive maintenance, remote diagnostics, and version upgrades.
Distributed Sites & Factories
Organizations with factories in multiple regions can centralize access, monitoring, and control while ensuring local compliance and security.
Emergency Response & Disaster Recovery
When physical access is disrupted by weather, logistics, or other issues, remote connectivity ensures business continuity.
Where Teams Use It
Remote Maintenance & Troubleshooting
Technicians can program, debug, and adjust machines without visiting the site — reducing travel costs and accelerating problem resolution.
OEM Support & Customer Service
Machine manufacturers can securely access customer systems for proactive maintenance, remote diagnostics, and version upgrades.
Distributed Sites & Factories
Organizations with factories in multiple regions can centralize access, monitoring, and control while ensuring local compliance and security.
Emergency Response & Disaster Recovery
When physical access is disrupted by weather, logistics, or other issues, remote connectivity ensures business continuity.
Key Features & Capabilities
| Feature | What It Means | Benefit |
|---|---|---|
| End-to-End Encryption (TLS / AES-256) | All communication is encrypted both ways | Prevents eavesdropping, data leakage |
| Zero Trust Access Controls | Least privilege, role-based, on-demand / scheduled access | Reduces insider risk and misuse |
| Clientless or Lightweight Access | Access via browser or lightweight client; minimal local installs | Fast and hassle-free deployment |
| Global Infrastructure / Low Latency | Distributed gateways or data centres close to customers; optimized routes | Smooth and reliable connectivity with low latency |
| Audit Trails & Session Monitoring | Logging, real-time dashboards, optionally session recording | Simplifies compliance and auditing; enables detailed troubleshooting |
| Scalability & Legacy Support | Supports large-scale deployments and a wide range of protocols, including legacy PLCs and serial/USB devices | Ensures flexibility, investment protection, and easy integration with existing infrastructure |
It delivers Industrial Security. It employs Zero-Trust policies and device-specific Role-Based Access Control.
It eliminates on-site waiting times by connecting to PLCs within minutes. It reduces the Mean Time To Repair (MTTR) by up to 70%.
It is Vendor-Agnostic (No Lock-in). It supports all major engineering platforms, including TIA Portal and Studio 5000, as well as mixed-brand environments.
Yes. All operations are encrypted and centrally controlled, monitored, and logged via administrator-approved “Just-in-Time” access.
It maintains detailed Audit Logs of all access and transactions. This supports regulatory compliance and audit-ready operations.
- FAQ
Frequently asked questions
Learn more about how RoltekConnect Cloud helps your team connect securely and scale easily. If you don’t see your answer here, our support team is ready to help.
