External Party Access Governance (OEM/SI)
Enable external parties to gain approved, time-limited, and scoped access with full session visibility—ensuring least privilege by default.
- The Challenge
Persistent, Unscoped External Party Access
External parties often connect with shared VPN accounts that never expire. Who accessed what and when is unclear; scope is too broad and revocation is slow. Audits become painful while operational risk and compliance overhead rise.

The RoltekConnect Cloud Advantage

Industrial-grade security
Zero-trust tunnels, modern ciphers, MFA/SSO, and firewall/ACL keep access locked down.

JIT access & approvals
Time-bound windows with one-click approvals; access opens only when needed, then auto-closes.

Scoped access & least privilege
Per-asset policies, role-based permissions, and port/protocol limits reduce blast radius.

Full session auditing & instant revoke
Session logs/recording for compliance, plus a kill-switch to terminate access immediately.
- TASK OVERVIEW
Typical Remote Tasks
Common actions technicians perform securely over RoltekConnect Cloud.
- Alarm / Fault Diagnosis
- Program / Parameter Update
- Firmware / Config Management
- Modbus / Register Validation
- Network Troubleshooting (WAN/LAN)
- Post-Maintenance Verification
- Deployments
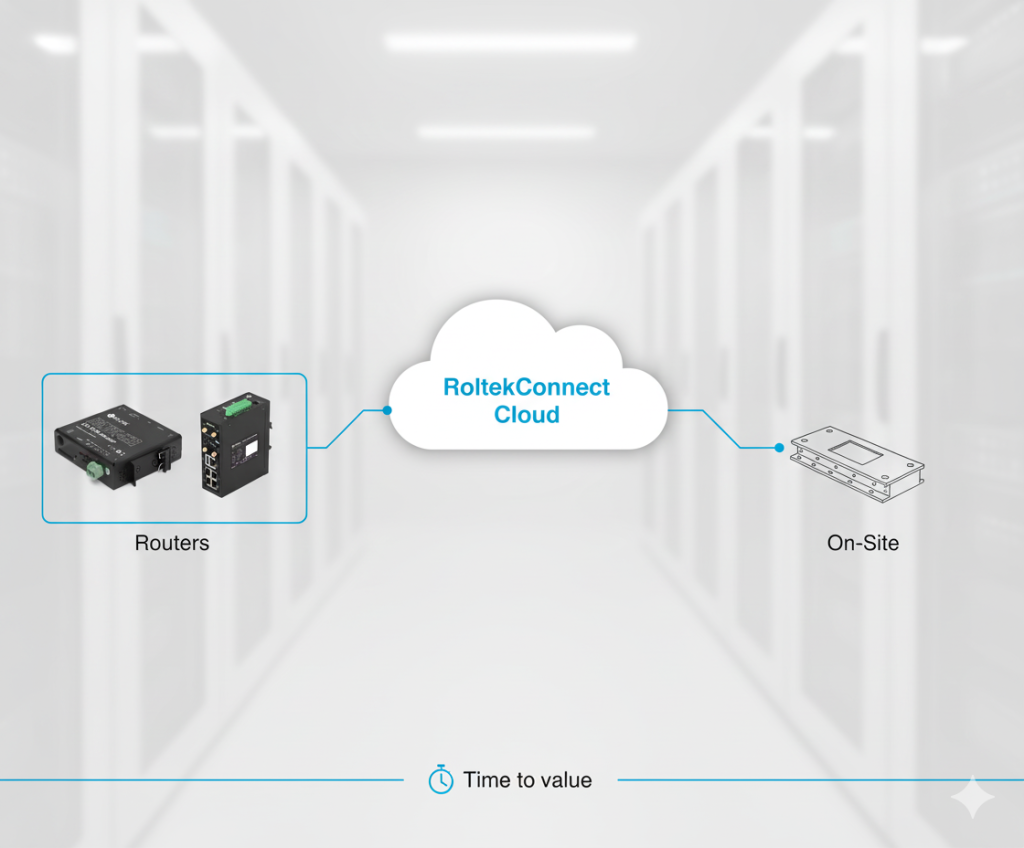
Deployment Options
Why it matters: Accelerates purchasing and rollout.
Routers: RLTK421 — LTE + RS-485/RS-232 / RLTK451 — LTE + Wi-Fi + dual Ethernet
Cloud: RoltekConnect Cloud (fully managed)
On-Site: DIN-rail mounting, −20…+70 °C, surge/ESD protection, hardware watchdog
Time to value: First connection in < 15 minutes
- Process
How RoltekConnect Cloud Solves It
Turns external party access into a request → approve → operate flow that’s temporary, scoped, and fully auditable.
-
1
Request
An external party requests access to a specific asset + time window (e.g., Line-3 / PLC-120, 2h). Adds purpose/work order; routes for approval.
-
2
Approve
Owner approves with one click; role, scope (ports/protocols) and expiry are auto-enforced. Access opens only for the approved window.
-
3
Operate
The external party connects through a zero-trust tunnel; session is logged/recorded. When time’s up—or revoked—access auto-closes.
Outcomes & KPIs (Before/After)
Makes value measurable.
It replaces perpetual shared VPNs with a request → approve → operate flow that is role- and time-bound. It enforces the principle of least privilege by default.
Access is managed via JIT (Just-in-Time) access and approvals. It opens only for the approved scope (including port/protocol limits) and duration, and then auto-closes.
It’s ensured by maintaining full session logs and recording. These records are used for audit and compliance, and immediate termination is possible with a kill-switch in case of risk.
How long does it take to set up and start using the system?
The time to establish the first secure remote connection and start using the system is specified as less than 15 minutes.
- FAQ
Frequently asked questions
Get quick answers to all your questions about our Vendor Access Governance (OEM/SI) solution. We have compiled the most common inquiries regarding security, process, and system deployment.
